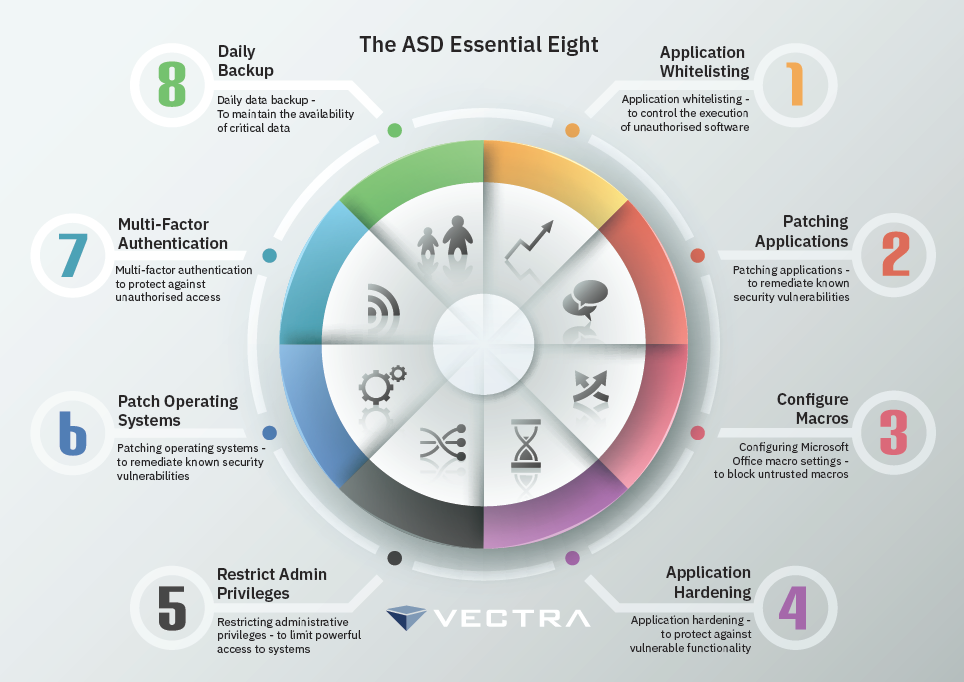
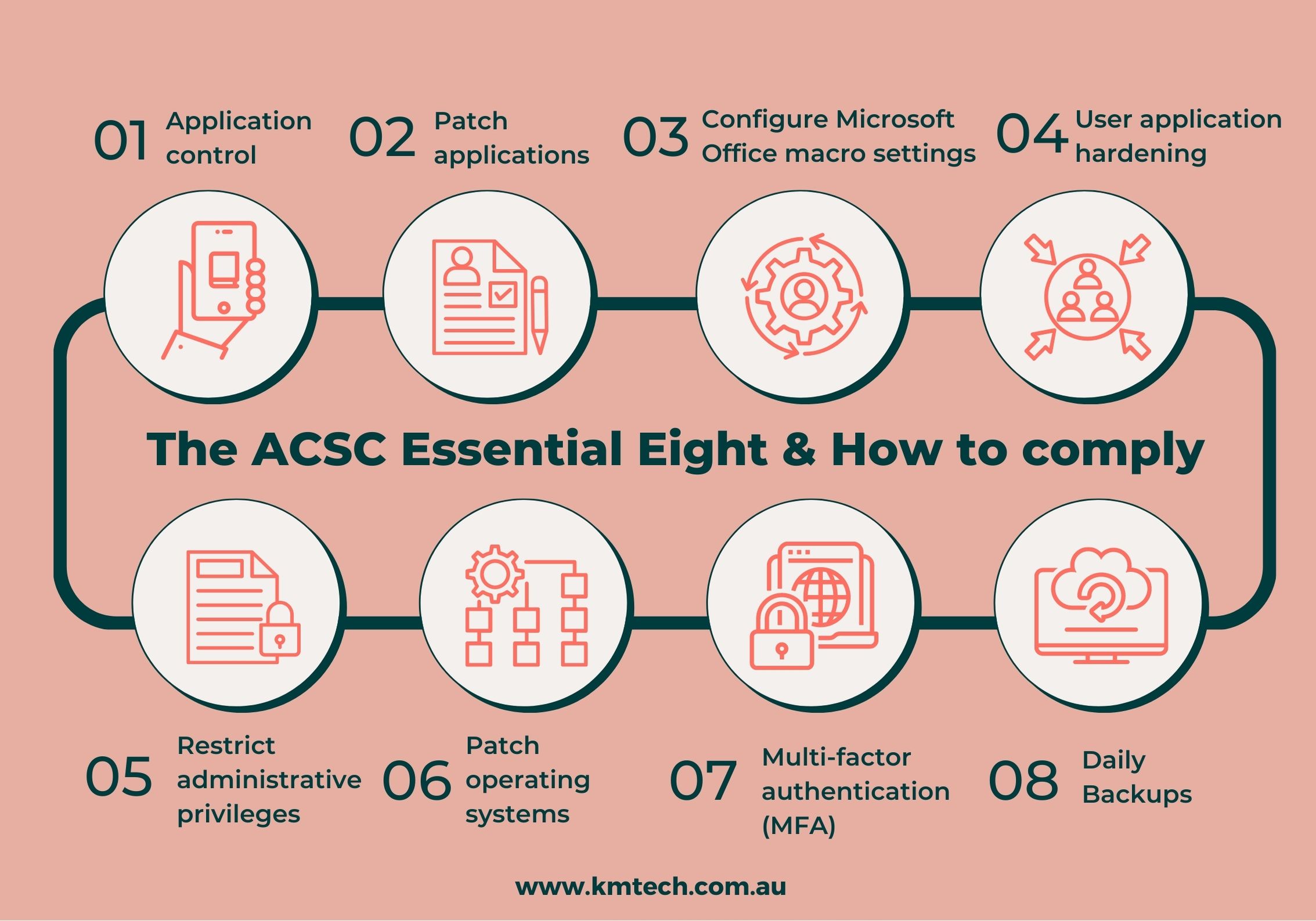
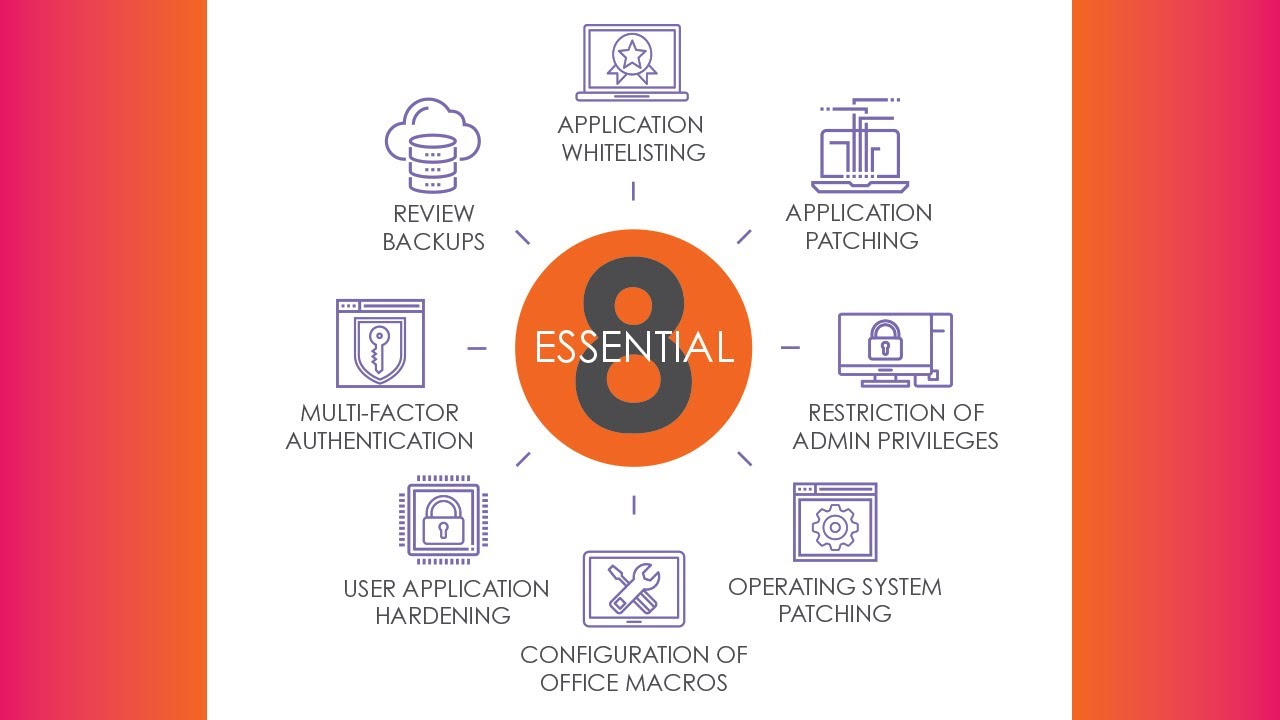
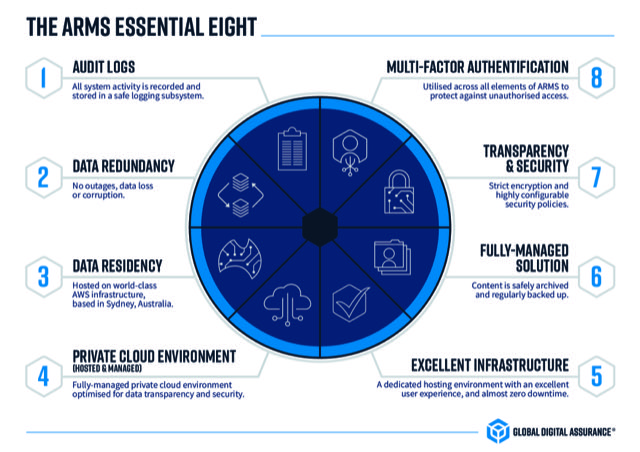
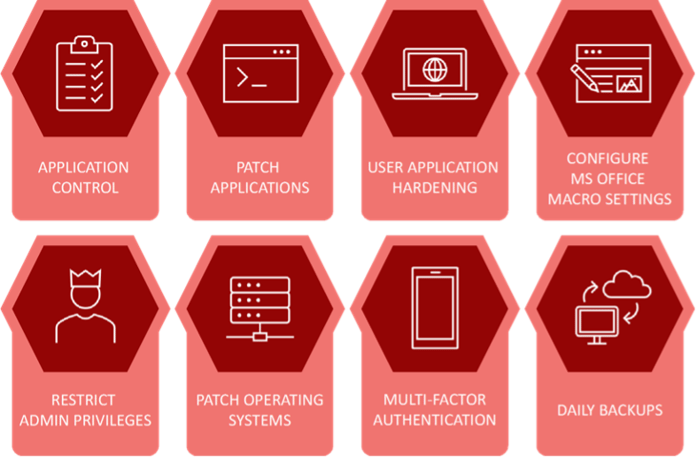
Daniel Schell on Twitter: "ASD release Essential 8 Maturity model. Loving those Whitelisting maturity levels stages. Audit is not whitelisting! https://t.co/wX1P5jGjQx" / Twitter

ASD Essential 8 – the minimum level of cyber security that you need to know and adhere to. - abcountrywide